Requirements
- Mac
- Windows
- Linux
- Sign up for 1Password.
- Install and sign in to 1Password for Mac.
- Install the 1Password browser extension (optional).
Required to autofill SSH keys in your browser.
Step 1: Generate an SSH key
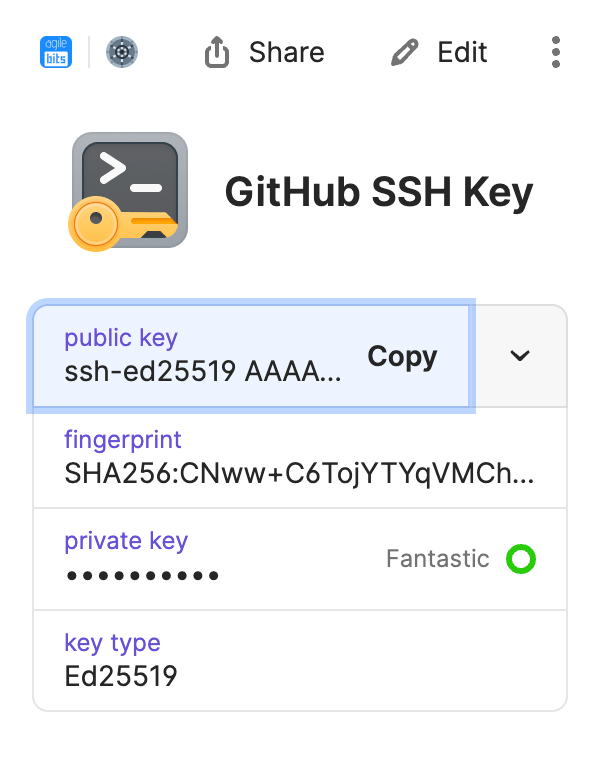
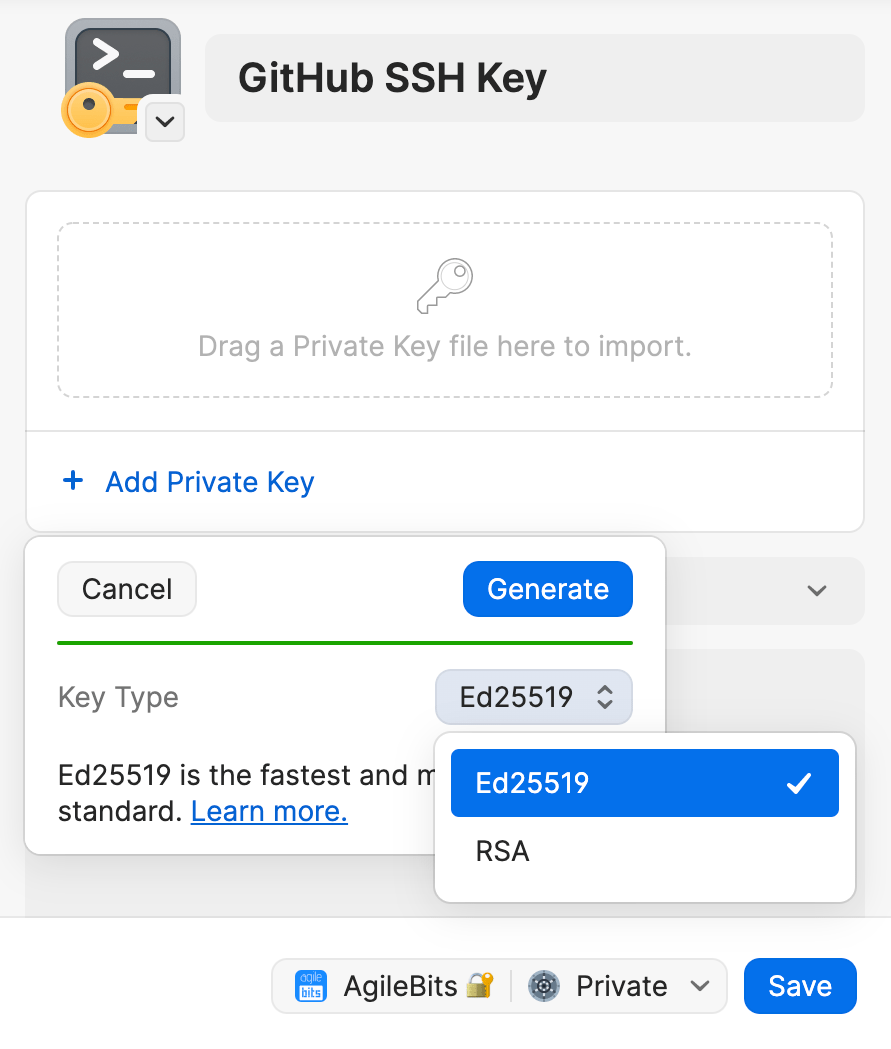
- Open and unlock the 1Password app, then navigate to your Personal, Private, or Employee vault. The name of this vault varies depending on your account type.
- Select New Item > SSH Key.
- Select Add Private Key > Generate New Key.
- Select an SSH key type: Ed25519 or RSA, then select Generate.
- When you’re done, select Save.
Step 2: Upload your public key
After you generate your SSH key, you can add the public key to your GitHub account. Visit the GitHub SSH key settings page upload your public key using the 1Password browser extension or desktop app.- Browser extension
- Desktop apps
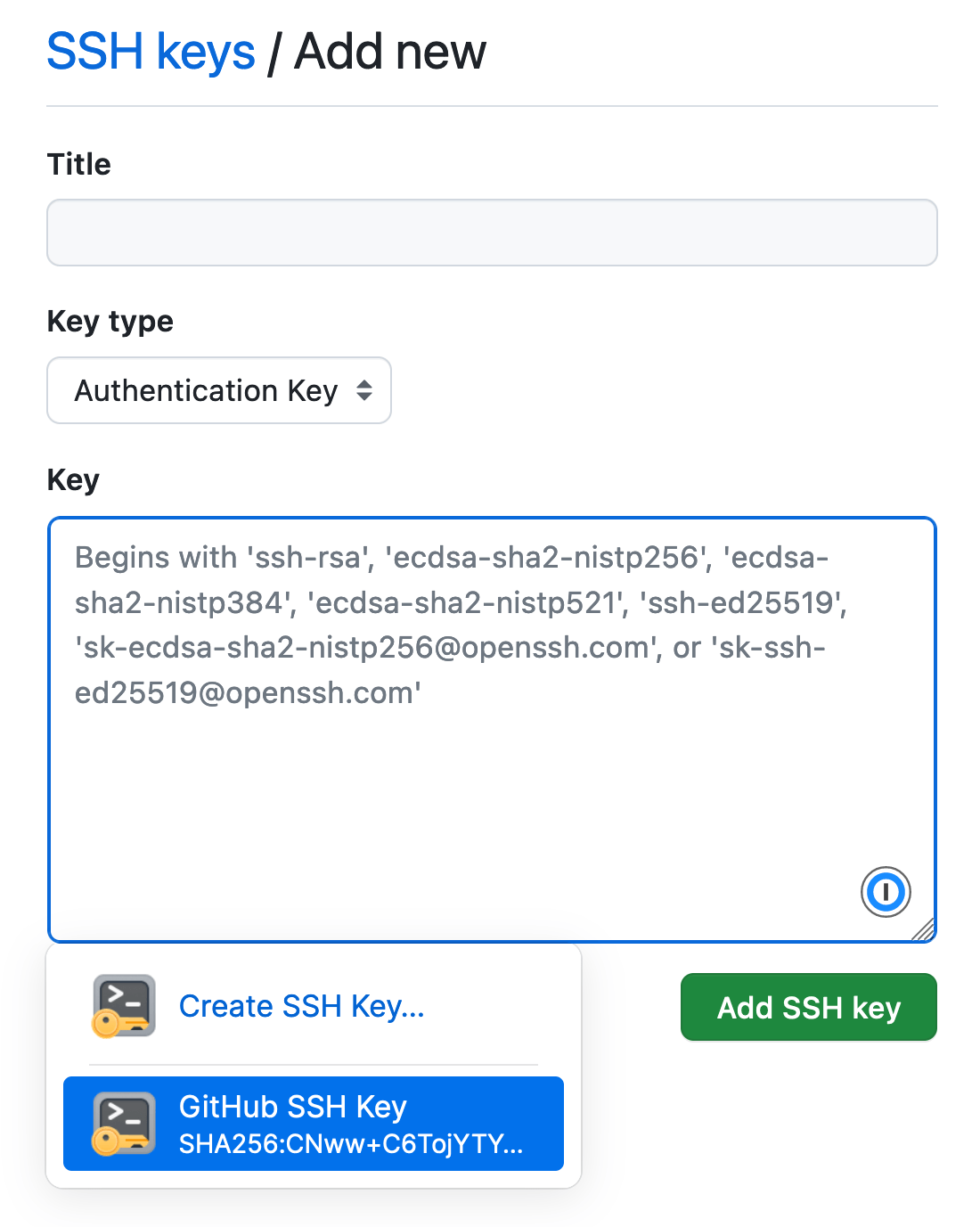
- Select the Title or Key field on the GitHub settings page. If 1Password doesn’t show a list of suggested items, select the 1Password icon in the field.
- Select the GitHub SSH key you just created. 1Password will automatically fill the public key and title in the corresponding fields.
- Select Add SSH Key on the settings page to save the key in your GitHub account.
Step 3: Turn on the 1Password SSH agent
The 1Password desktop app includes an SSH agent that, when turned on, runs in the background to handle authentication for your SSH clients. Follow these steps to turn on the SSH agent:- Mac
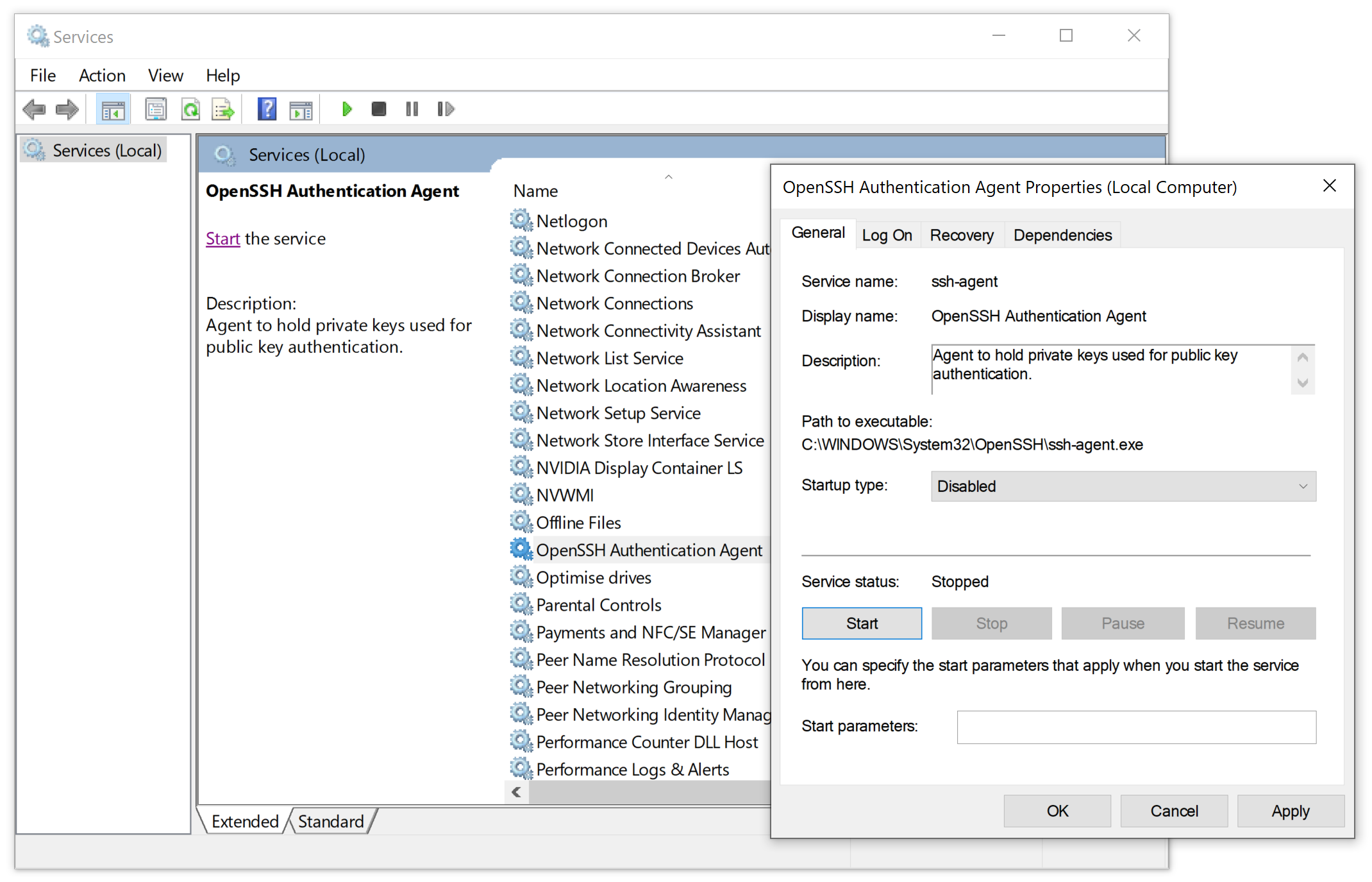
- Windows
- Linux
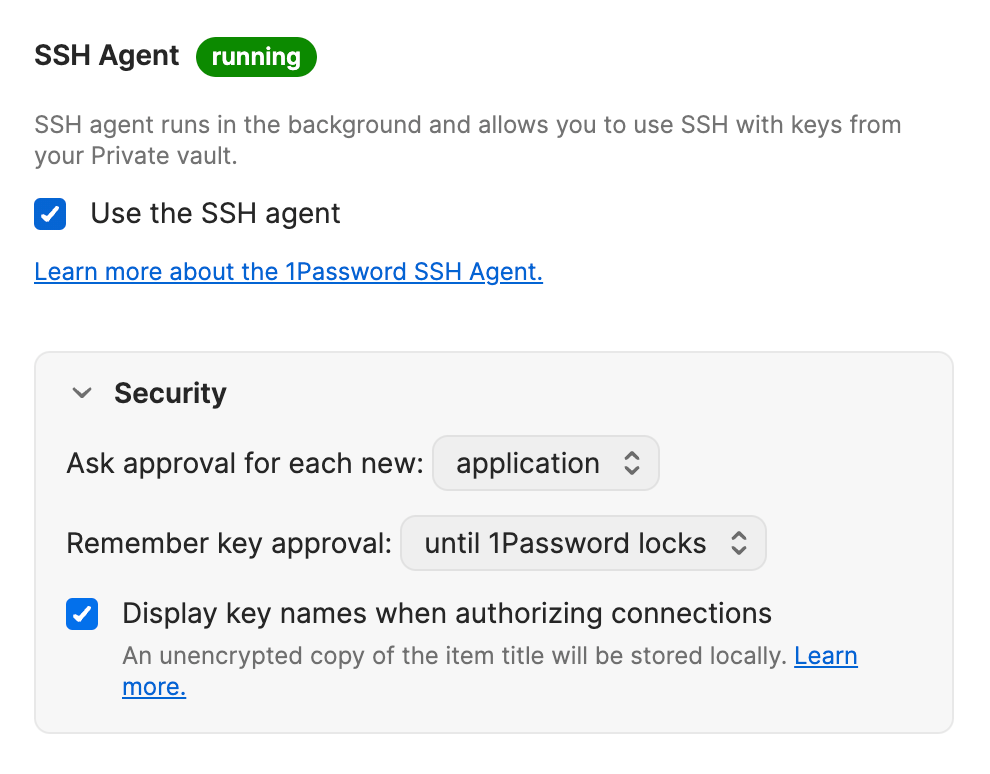
- Open the 1Password app and select 1Password > Settings from the menu bar, then select Developer.
- Select Set Up SSH Agent, then choose whether you want to display SSH key names when you authorize connections.
- (Optional) Adjust the authorization options for when and how often the SSH agent will ask you to approve SSH requests.
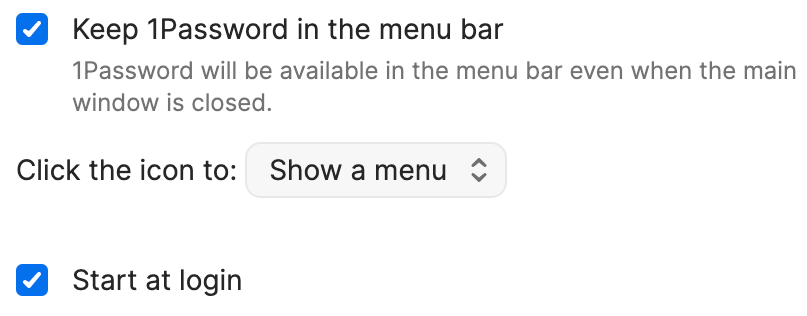
- Open the 1Password app and select 1Password > Settings from the menu bar, then select General.
- Select the checkboxes to Keep 1Password in the menu bar and Start at login.
Step 4: Configure your SSH or Git client
After you turn on the SSH agent in 1Password, you’ll need to configure your SSH client to use the agent for authentication.- Mac
- Windows
- Linux
Add the If your For an agent path that’s easier to type, you can optionally run the following command to create a symlink for Now your SSH clients will use the 1Password SSH agent for all hosts.If you prefer to migrate to the 1Password SSH agent gradually, you can configure your SSH clients to only use the SSH agent for one or more specific hosts, instead of all hosts. Learn more about gradual migration.Some SSH clients don’t support every configuration option that the
IdentityAgent snippet to your ~/.ssh/config file:~/.ssh folder or config file doesn’t exist yet, create it first.You can also set the SSH_AUTH_SOCK environment variable in the shell where your SSH command runs:~/.1password/agent.sock:~/.ssh/config file has to offer.
Learn more about SSH client compatibility.By default, OpenSSH servers are configured to limit the amount of authentication attempts for an incoming SSH connection. Learn more about how to avoid the SSH server six-key limit.Step 5: Run a command
Now you’re ready to start using the 1Password SSH agent with GitHub. From your project directory, run:git pull now, you can run this command instead to quickly test your GitHub SSH setup:
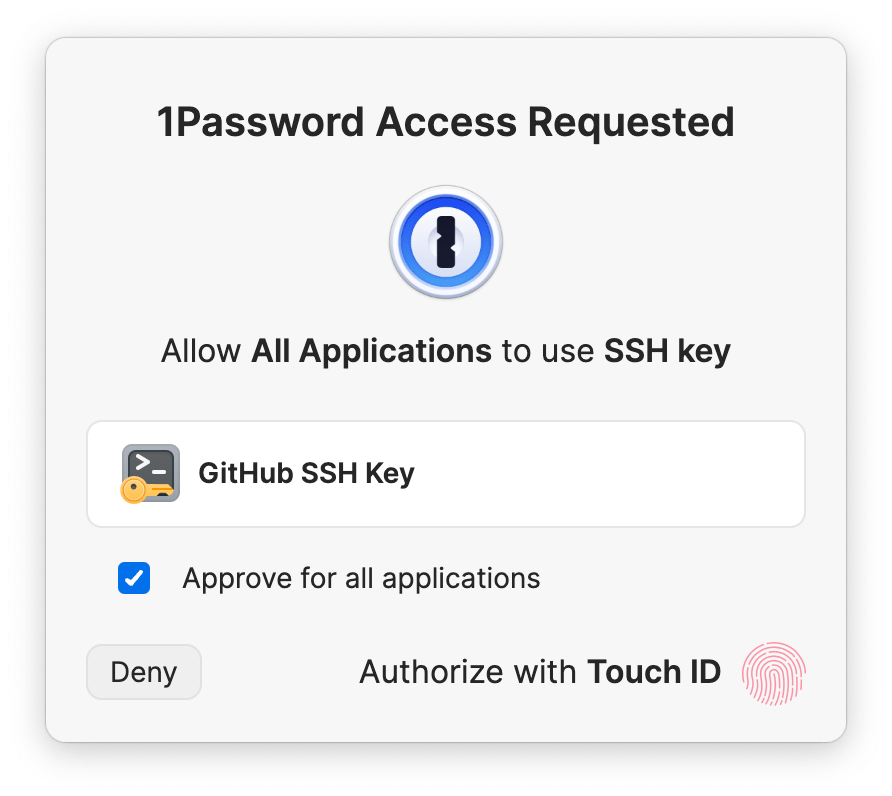
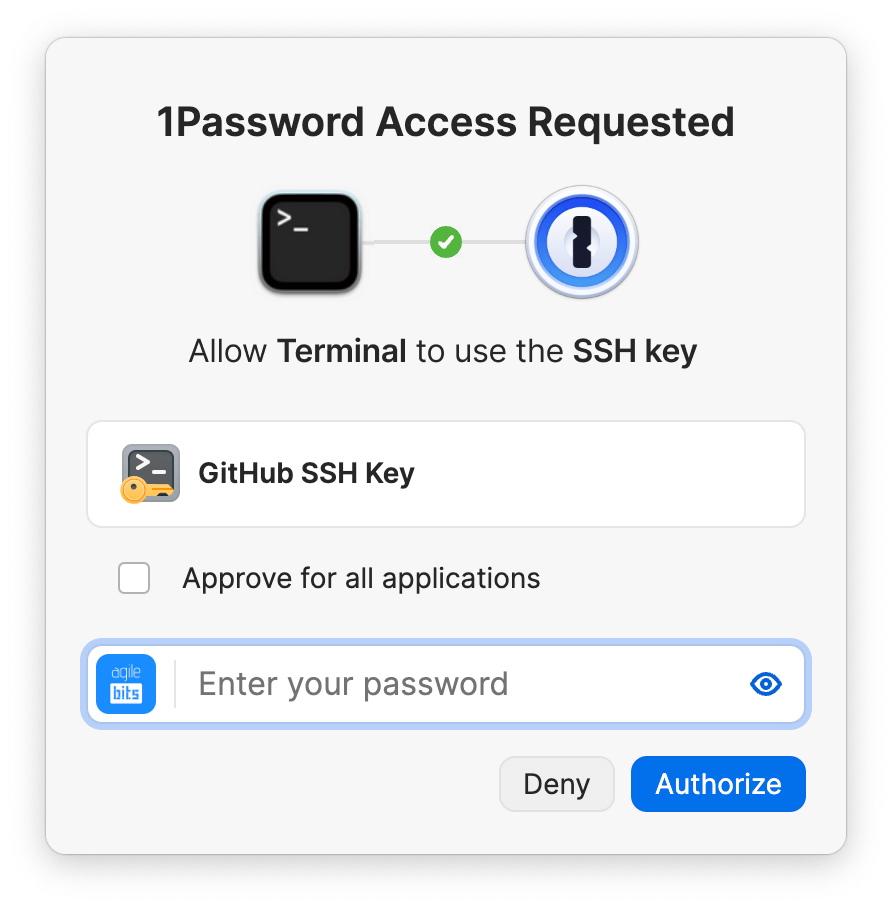
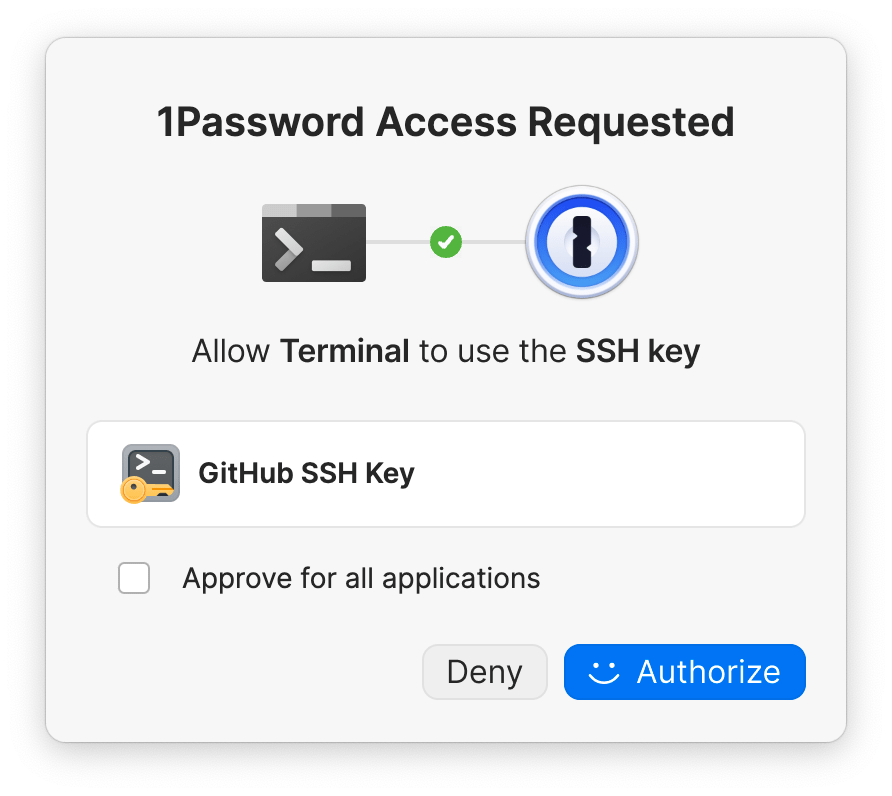
Step 6: Authorize the SSH request
1Password will ask you to allow your terminal or other SSH client to use your SSH key. You can approve this request using the authentication option indicated on the prompt (for example, Touch ID, Windows Hello, or your account password). If 1Password is locked, you’ll also be prompted to unlock the app so the SSH agent can access your private keys.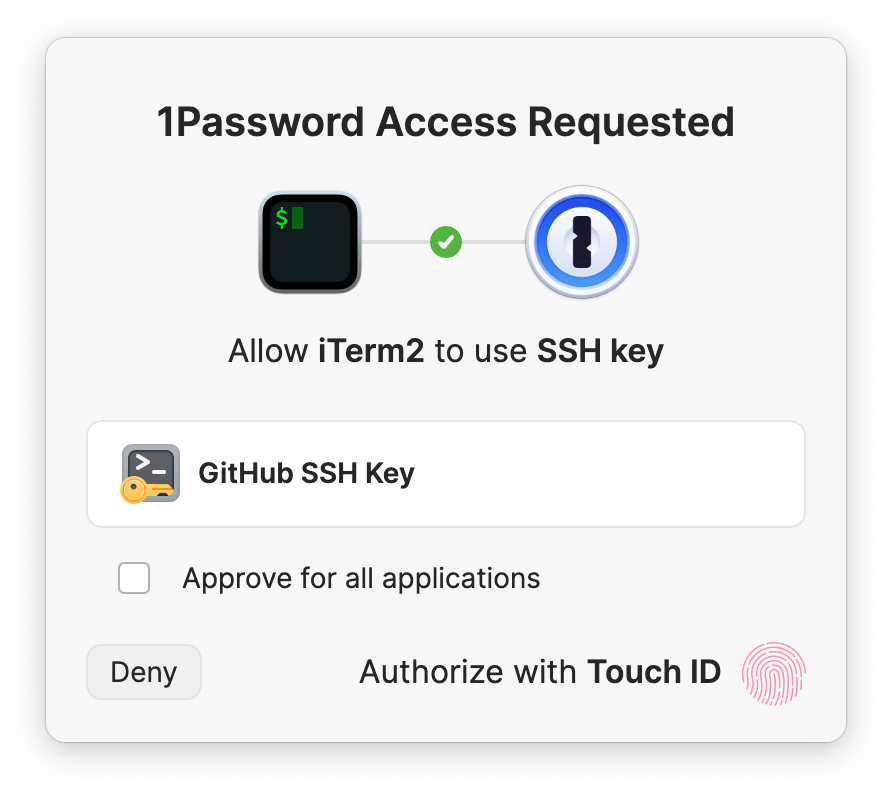
Adjust your authorization options
There are several options you can choose from to determine how long the agent remembers your SSH key approval and what usage you’re approving for each key. These options determine when the SSH agent will ask you to approve SSH requests.In the 1Password settings
Open 1Password, then select your account or collection at the top of the sidebar and select Settings > Developer. In the security settings for the SSH agent, you can choose the options that best suit your needs. You can change your settings at any time.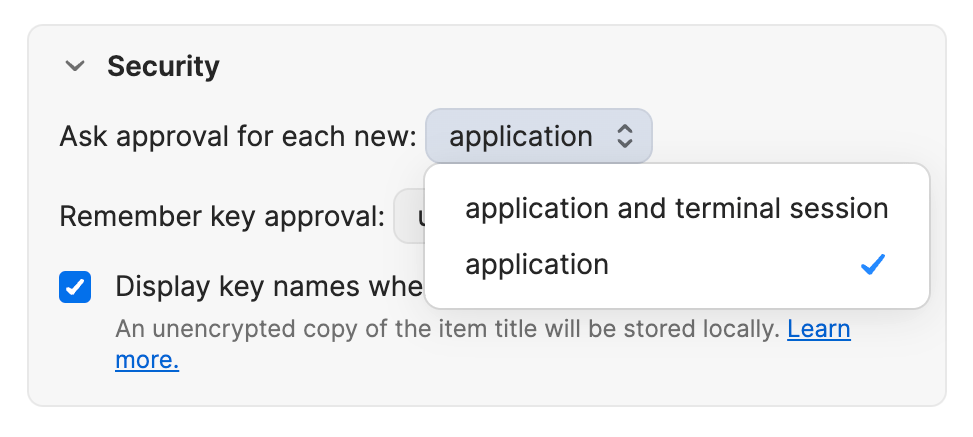
- For each new application (default): You’ll be asked to authorize SSH requests from each new application to use a specific SSH key.
- For each new application and terminal session: Similar to the first option, you’ll be asked to authorize SSH requests from each new application to use a specific SSH key. If the application is a terminal emulator or an IDE with a built-in terminal, you’ll also be asked to authorize requests for each new terminal tab in that application.
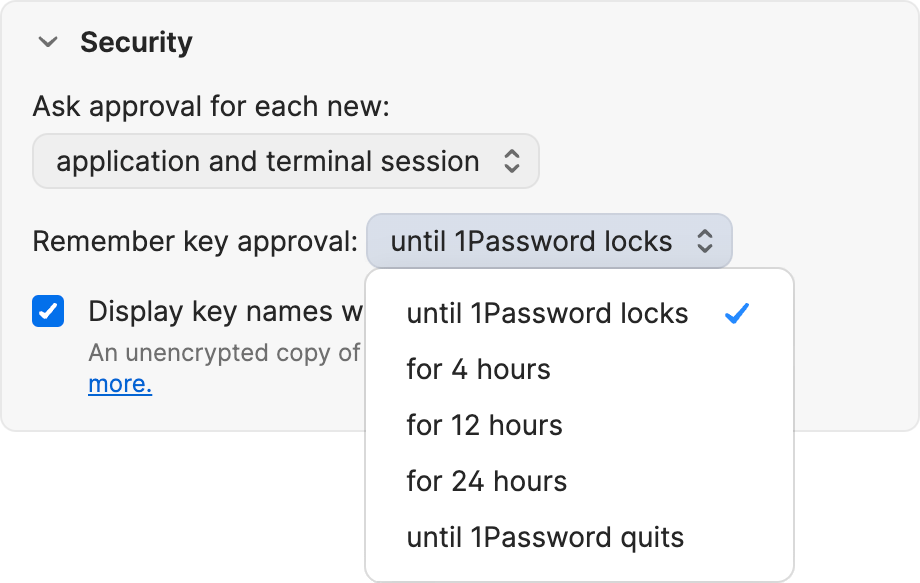
- Until 1Password locks (default): Every time 1Password locks, your key approvals are wiped from the agent’s memory and you’ll be asked to reauthorize any previously approved SSH clients to use your keys. For example, if you approve the terminal application to use your SSH key for GitHub, then 1Password locks, you’ll need to reapprove any new requests from the terminal to use your GitHub SSH key when 1Password unlocks. Learn how to change your 1Password lock settings.
- Until 1Password quits: Every time 1Password quits, your key approvals are wiped from the agent’s memory. Any agent sessions and background processes will also end. To use the SSH agent to authorize any new requests to use your SSH keys, you’ll need to reopen 1Password.
- For a set amount of time: You can choose from 4, 12, or 24 hours. If you select one of these options, your key approvals will remain in the agent’s memory for that duration, even when 1Password is locked. You won’t need to reauthorize new requests from the same applications to use the same SSH keys you’ve already approved, but you’ll be prompted to unlock 1Password so the SSH agent can access your private key.
In the authorization prompt
Every authorization prompt for a client to use an SSH key includes the option to approve the use of that key for all applications. To turn on this option, select the checkbox to Approve for all applications.